Our 2023 #DEIA survey is now open! Click here to participate!
About
As one of the three brands comprising the global Kantara stable, Kantara Initiative, Inc is an international ethics based, mission-led non profit industry ‘commons’. Kantara’s Mission is to grow and fulfill the market for trustworthy use of identity and personal data in pursuit of its Vision to see equitable and transparent exchange of identity and personal data for mutual value. Kantara’s members are spread across continents and countries around the globe.
Kantara began its life’s work as an affiliate program under IEEE-ISTO in 2009, before self incorporating in the US state of Delaware as a non-profit 501(c)(6) industry association in 2016. Later that year it incubated a concept to develop an digital identity professionals industry association that was later to become later known as IDPro upon becoming self sustaining and incorporating in 2017. Later in 2017 the Kantara Initiative Europe non-profit trade association was established within the European Union in Estonia as a legally and financially separate entity. In 2018 the Kantara Initiative Educational Foundation 501(c)(3) public good charity was incorporated, again in Delaware, to enable the smooth transition of the assets of the US Identity Ecosystem Steering Group (IDESG) upon the IDESG’s dissolution.
Kantara Initiative, Inc. is unique in offering service providers 3rd party conformity assessment and assurance approval against its NIST 800-63-3 Class of Approval under its Identity Assurance Trust Framework, extendable other schemes and their respective standards and specifications. This brings greater confidence to procurers of digital services and in turn their customers that digital identity credential service providers’ solutions are standards compliant.
The Kantara community also develops specifications from a ‘blank canvas’ and submits them to formal standardization bodies to fill emerging industry and marketplace needs. The GDPR-compliance assisting Consent Receipt specification is a perfect example, now annexed in ISO/IEC 29184 Online privacy notices and consent, and foundational for the draft ISO/IEC 27560 Privacy technologies – Consent record information structure. But it does not end there. User Managed Access (EIC Award Winner for Innovation in Information Security 2014) is base-lined for Healthcare and Financial Services globally.
Kantara Initiative Inc is truly international and apolitical. More than 50% of its members reside outside the US comprising public, private and non-profit sectors. It connects a global, open and transparent leadership community committed to low or no barriers to participation is sustained by Digi.me, Experian, ForgeRock, Idemia and the Internet Society – offered by no other organization in the industry.
Identity at the Center of Digital Transformation
Organizations of all types are faced with permanent change – in technology, markets, business models, and regulation. This continuously changing environment applies to organizations big and small, both domestic and global. Services that leverage digital identity and personal data are becoming pervasive and the identity data of people, organisations, applications and devices represents a user’s digital DNA and lie at the heart of a thriving digital economy.
We see the transformation cycle as a 4-stage process:
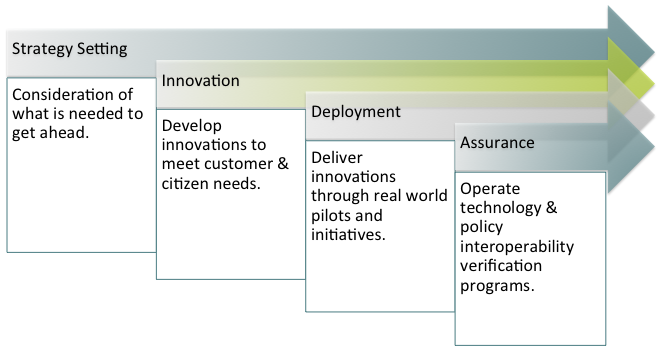

Get Ahead of the Curve
Few, if any, organizations can succeed at every stage of transformation in isolation. Kantara Initiative brings together the right thought leaders and industry representation – vendors, adopters, governments, standards bodies – to address all four stages.
Our Mission: To grow and fulfill the market for trustworthy use of identity and personal data.
Our Vision: To see equitable and transparent exchange of identity and personal data for mutual value.
Nuture, innovate, operate – that’s what we do.
Goals:
-
- Bring vendors, deployers, individuals, and organizations together to accelerate digital marketplace adoption through the operation of conformity assessment based assurance and operation of Trust Frameworks together with the development of specifications in open community collaboration.
- Develop, operate and maintain Trust Framework, R&D and interoperability programs with strong branding to advance the state of the art for the betterment of industry and its customers.
- Connect technical, business, legal, and policy experience to achieve holistic & trusted identity management solutions
- Operate and maintain an open and democratic governance model with no financial barrier to participation
- Provide an operational structure with nimble processes, procedures, and oversight, together with a viable financial model
- Commit to open standards and encourage interoperable implementations from both the COTS product and open source development communities
- Foster positive dialogue across all relevant organizations to assure coordination, harmonization, and re-use of all applicable open content (specs, policy, etc.)

